Scaling Beyond BloodHound CE
Right Tool, Wrong Job
BloodHound CE is designed to identify Attack Paths to exploit. It’s excellent for penetration testers and Red Teams and can provide insight and quick wins for defenders. But full-scale defense requires scalable, comprehensive protection.
-

Manual, point-in-time operations don’t scale
BloodHound CE provides you a point-in-time view of an individual attack paths from one system to another. Defenders need continuous, real-time mapping of all Attack Paths.
-

Prioritizing Attack Paths manually is complex and time-consuming
While BloodHound CE can illustrate areas where an organization’s defensive posture needs improvement, Defenders need to understand which of the hundreds of thousands of Attack Paths present the biggest risk.
-

Administrators demand remediation guidance
Knowing you have a problem is important, but those charged with fixing Attack Paths need in-depth guidance to quickly and safely remediate.
Scale Faster with BloodHound Enterprise
BloodHound Enterprise is an enterprise commercial product designed for Security and IT Operations Teams to continuously and comprehensively manage Attack Paths. As a SaaS solution, BloodHound Enterprise deploys in minutes with a complete view of your identity risk. BloodHound Enterprise analytics and remediation guidance provides optimal reduction of identity risks, with empirical risk and trend reporting.
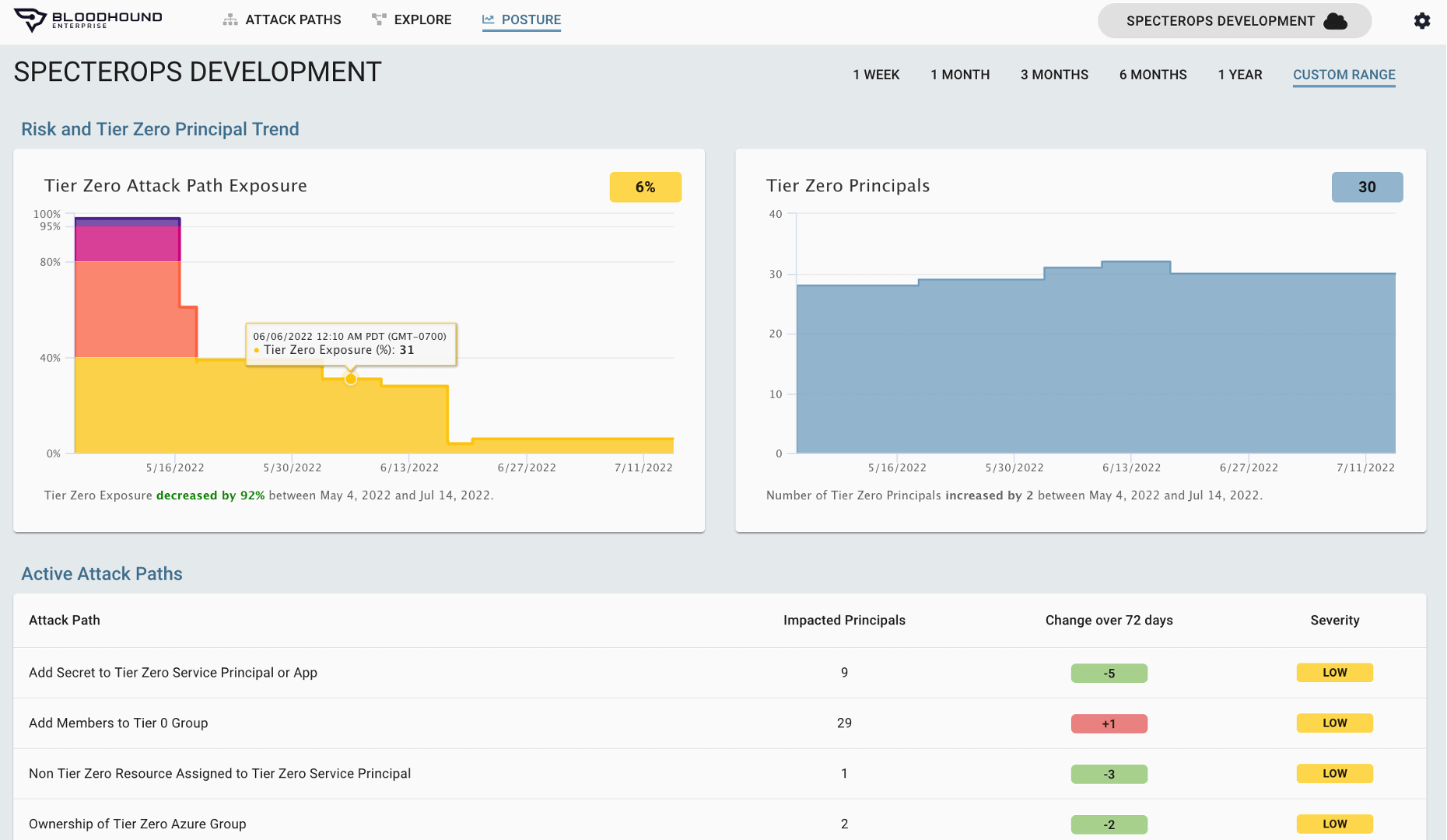
Comprehensive Visibility
Continuous Attack Path Mapping
BloodHound Enterprise exposes all the active pathways adversaries can take to move laterally and escalate privileges to Tier Zero principles. Even as your networks, user privileges, application permissions, and security group memberships change, BloodHound Enterprise continually:
- Maps every relationship and connection
- Provides full understanding of real permissions
- Tracks and exposes new Attack Paths
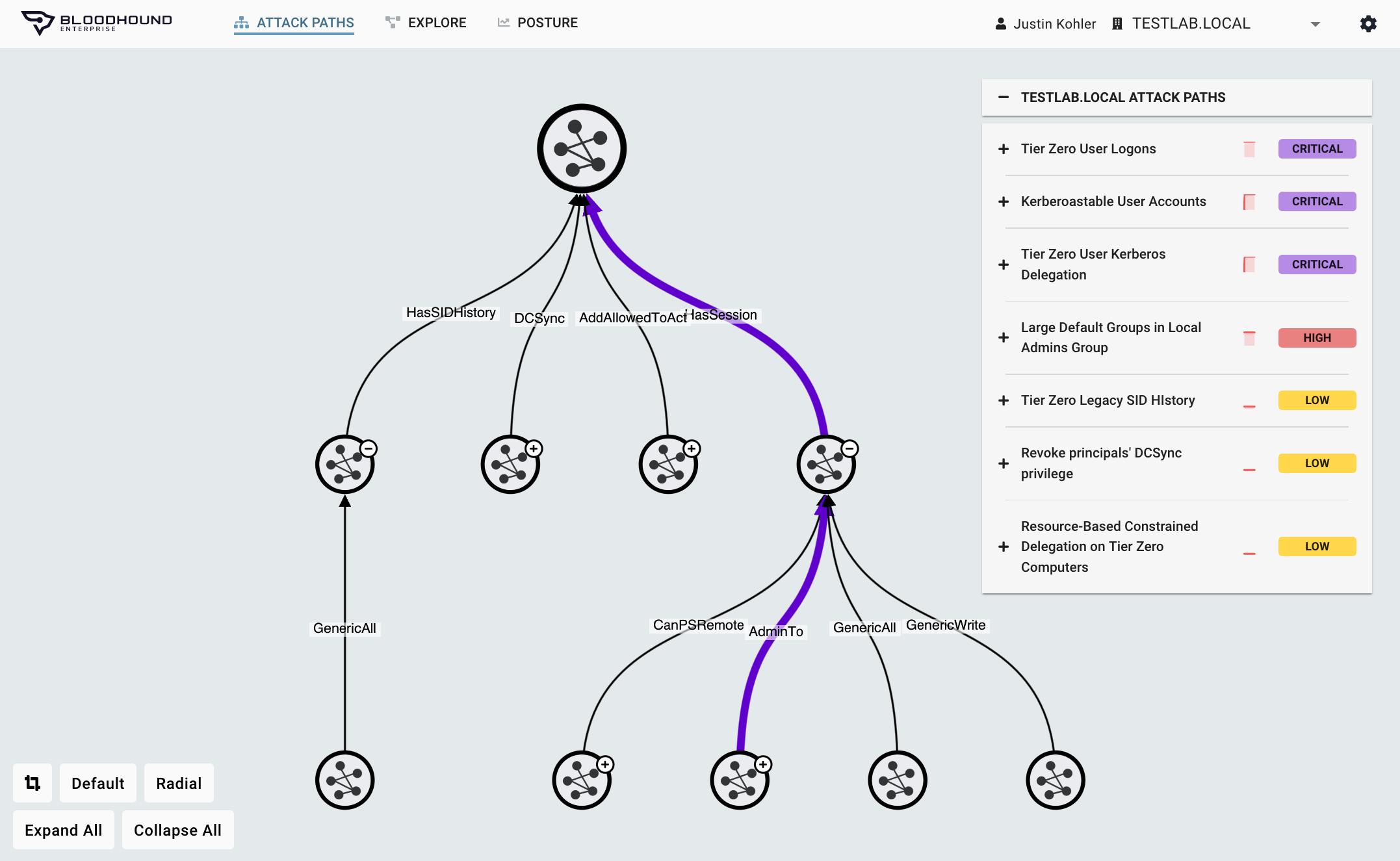
Prioritized Response
Risk-based Choke Point Analysis
Exposing all the Attack Paths is just the first step. To stop adversaries in their tracks, BloodHound Enterprise identifies the optimal remediations by:
- Measuring the empirical exposure of each Attack Path
- Pinpointing Choke Points to block the largest number of pathways
- Ranking remediation Choke Points by collective risk reduction
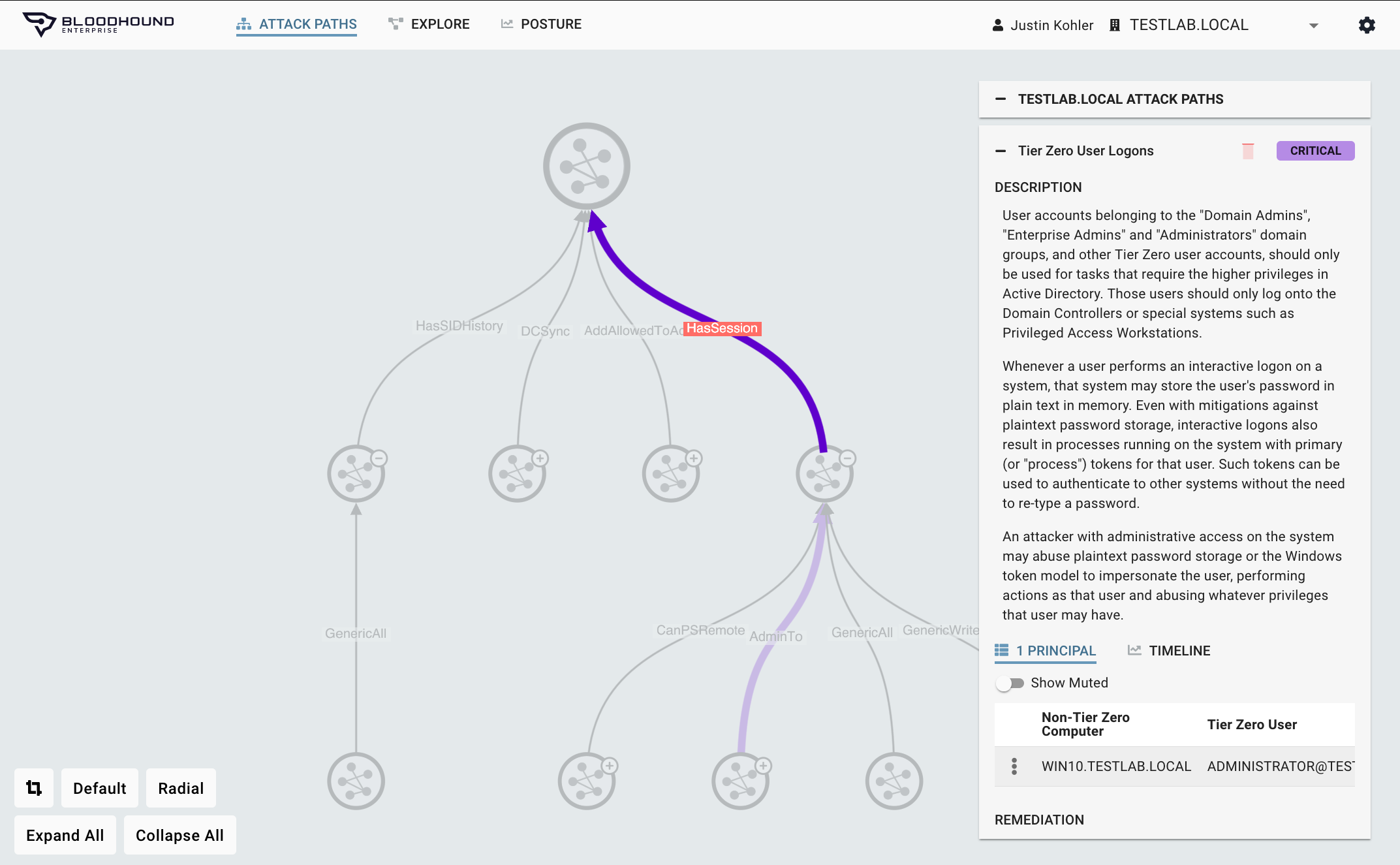
Be Informed
Enterprise Class Reporting
Visualize and report on your risk across all your entire enterprise (all domains / Azure tenants).
- Report your Identity risk with confidence
- Monitor remediation and track changes over time
- Understand risks before you establish a domain/forest trust