The problem of Attack Path Management requires a fundamentally different, unique methodology designed to help organizations understand, empirically quantify impact, and eliminate identity-based Attack Path risks.
Our Solution
BloodHound Enterprise is based on four core tenets
Continuous Attack Path mapping
Enterprise networks, user privileges, application permissions and security group memberships are dynamic. Consider that every system a privileged user logs into they leave behind tokens and credentials for adversaries to obtain. Because the connections and behaviors that form Attack Paths are continuously changing, the Attack Paths themselves must also be continuously mapped. BloodHound Enterprise continuously:
- Charts every relationship and connection
- Reveals full understanding of real permissions
- Exposes new and existing hidden Attack Paths in AD and Azure AD
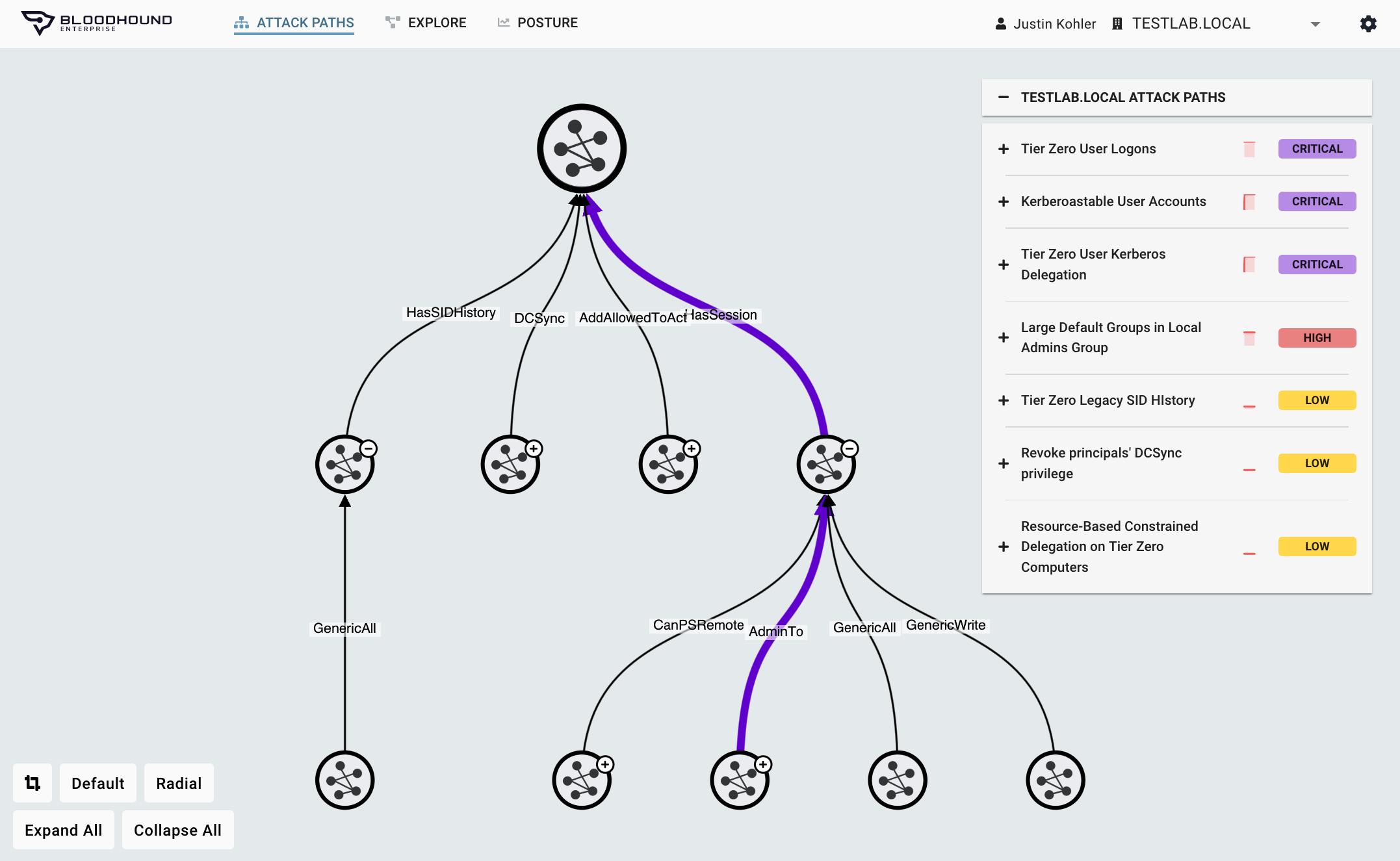
Attack Path Choke Point prioritization
The haphazard elimination efforts of AD misconfigurations provide zero security posture improvement and negatively impacts team productivity. However, if you can empirically identify the specific misconfigurations that allow you to eliminate the largest number of Attack Paths you can generate meaningful security posture improvement and increase your team’s productivity.
Through continuous Attack Path mapping and assessing every particular privilege and user behavior, BloodHound Enterprise:
- Measures the impact of any point in an Attack Path
- Identifies the optimal location to block the largest number of pathways
- Ranks these finite set of Choke Points by collective risk reduction
- Minimizes remediation efforts and eliminating misconfiguration debt cleanup
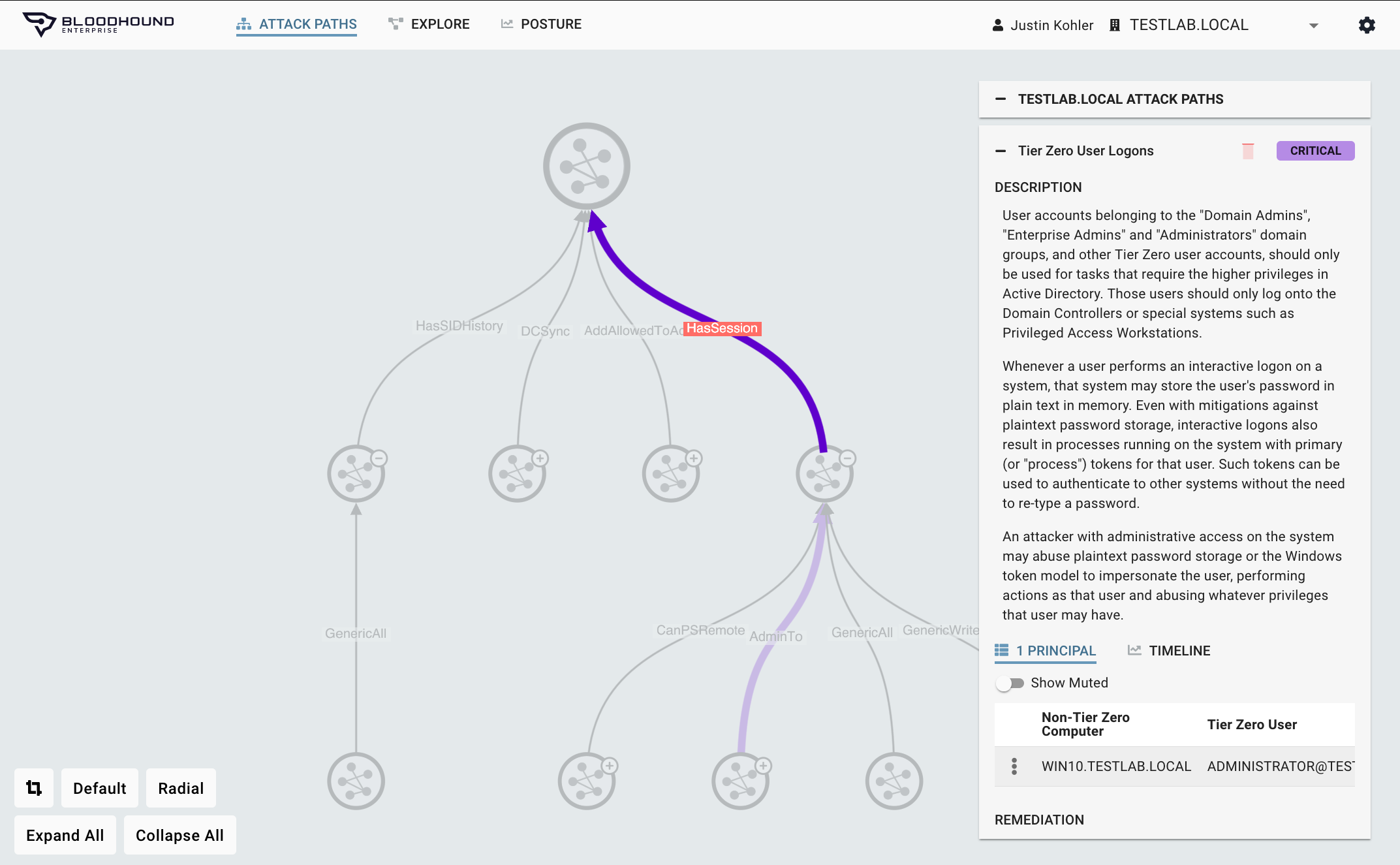
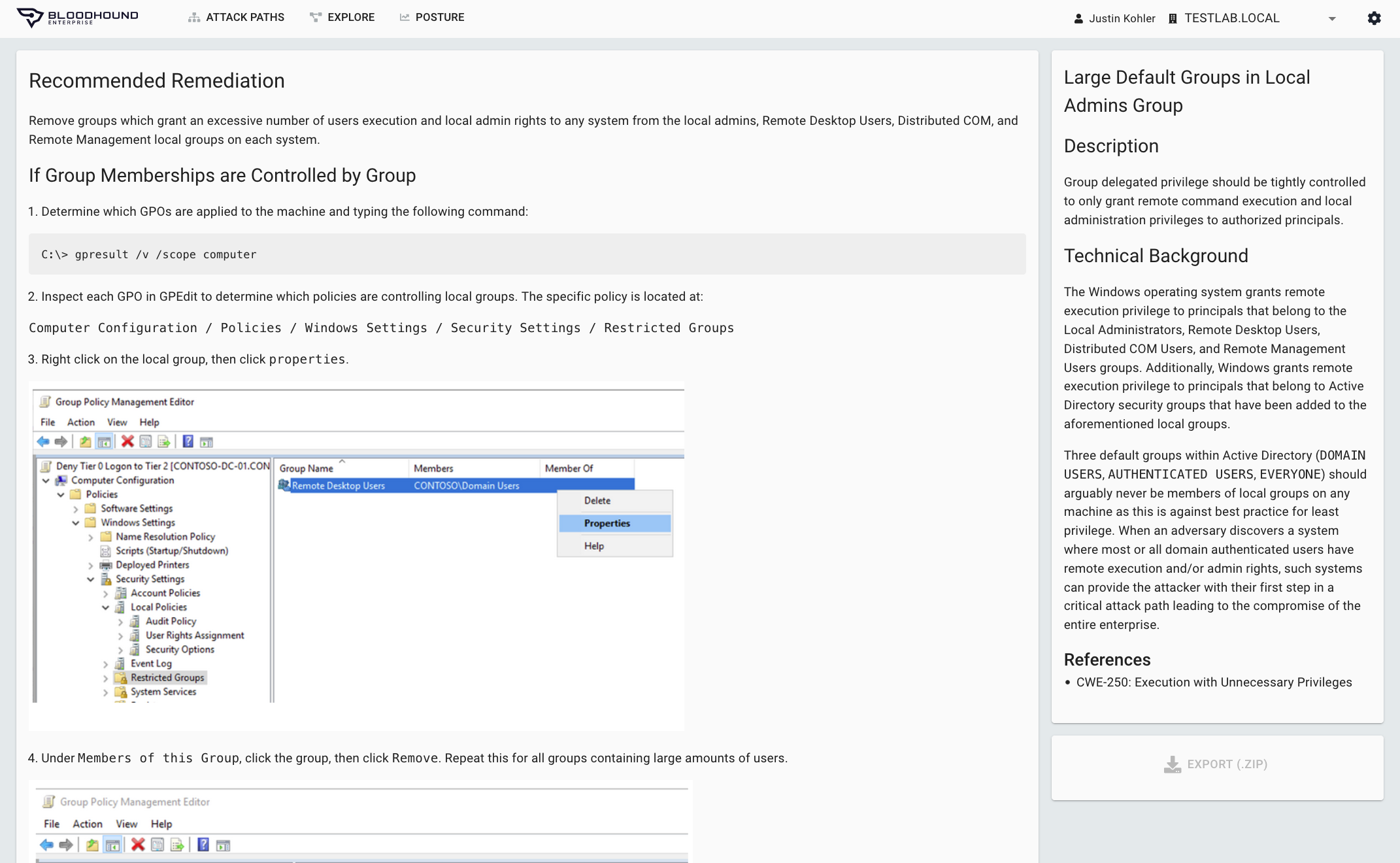
Real-world remediation guidance
Generic, lofty, or impractical remediation steps provide no value. In fact, they can lead to outages if teams attempt to implement them without understanding the implications. To provide impactful remediation guidance, the steps must be constructed with an understanding of the true privileges of users, the pathways they create, and with clear unambiguous language. By performing continuous, comprehensive AD and Azure AD mapping, BloodHound Enterprise, an Attack Path Management Solution:
- Delivers practical remediations without drastic changes to AD / Azure AD or negative impact
- Provides precise and comprehensive guidance to ensure Attack Path elimination
- Furnishes instructions on how to validate privileges being removed are not required
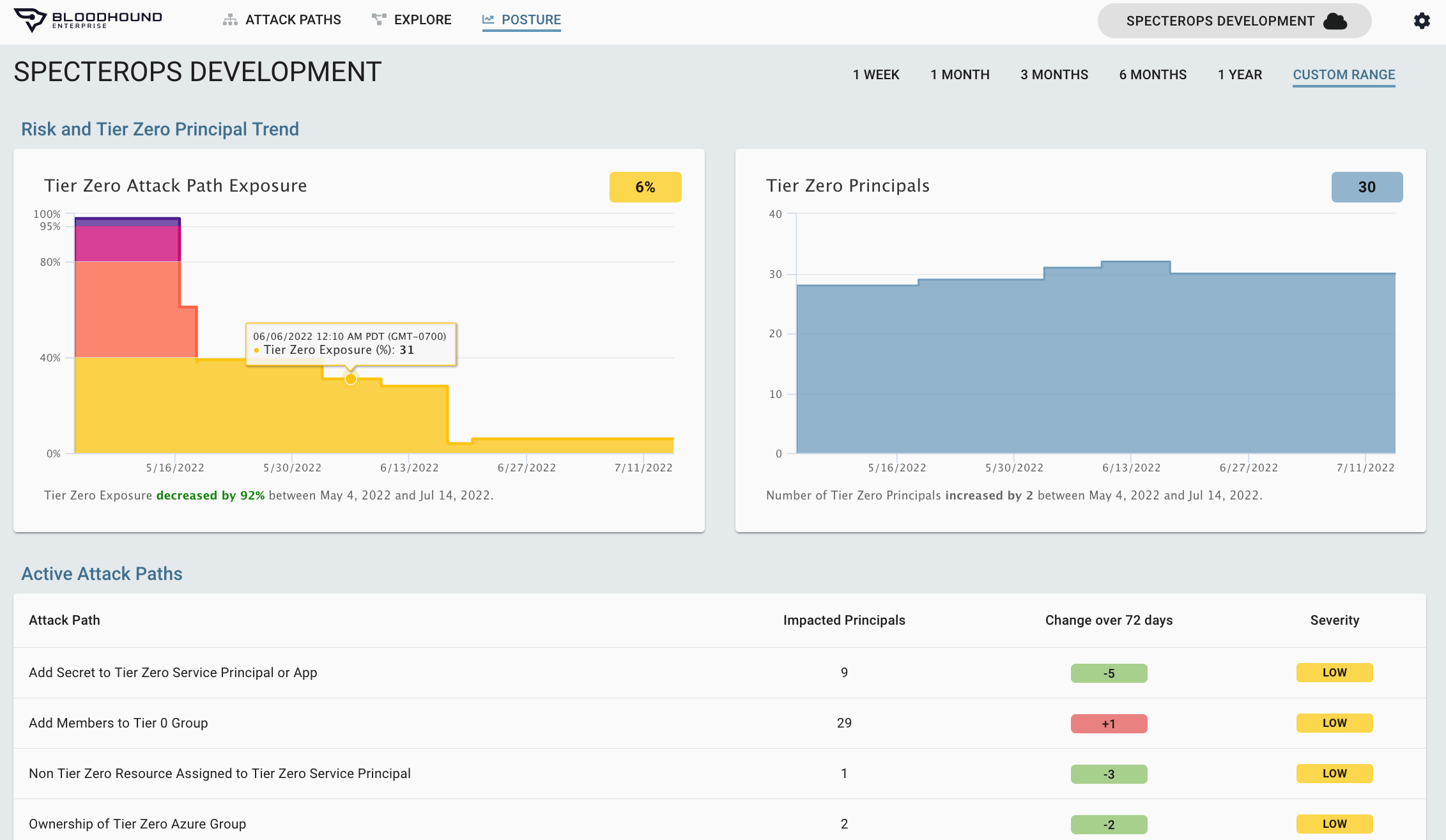
Continuous security posture measurement
To improve one’s security posture, one must be able to first baseline and then measure the change to your security posture. Often security offerings lack the ability to empirically measure the entire system they are protecting, thus they are unable to provide true assessments of risk. While AD and Azure AD is a complicated and dynamic system, it is a contained system that allows for continuous and comprehensive measurement of Attack Path risks.
BloodHound Enterprise:
- Establishes immediately a baseline of AD and Azure AD, identifying each Attack Path and the risk of any given point on the Attack Path
- Measures continuously as changes to Active Directory are made, reassessing risk
- As Choke Points are eliminated, significant security posture improvements are observed