Eliminate Lateral Movement and Privilege Escalation
Attack Paths: The fast lane for lateral movement and privilege escalation
After gaining an initial foothold in an organization, adversaries utilize Identity Attack Paths to deploy ransomware, steal confidential information, or perform other nefarious acts. Identity Attack Paths in AD and Entra ID not only enable privilege escalation and lateral movement, but are invaluable to adversaries because they:
-
Are Ubiquitous
95%+ percent of enterprises utilize AD and Entra ID. Lack of visibility and enormous complexity of these directory services means finding an Attack Path in these organizations is virtually guaranteed. Most enterprises have hundreds of thousands of Attack Paths, some millions.
-

Provide Unmatched Payoff
While taking control of AD or Entra ID is not the adversary’s end goal, no other tactic guarantees success like abusing Identity Attack Paths. Each Attack Path presents the opportunity to achieve Domain/Global Admin giving the adversary full control of your company.
-

Are Executed Quickly and Silently
For Identity, relying on detection-based controls alone is almost always too late. Not only can adversaries blend in with administrative activities, but skilled adversaries can abuse Attack Paths to reach their objective far quicker than detection and response tools and teams can act.
Take back control with BloodHound Enterprise
Gain Enterprise-wide visibility and achieve least privilege. Sever millions of Attack Paths with prioritized remediations and expert guidance.
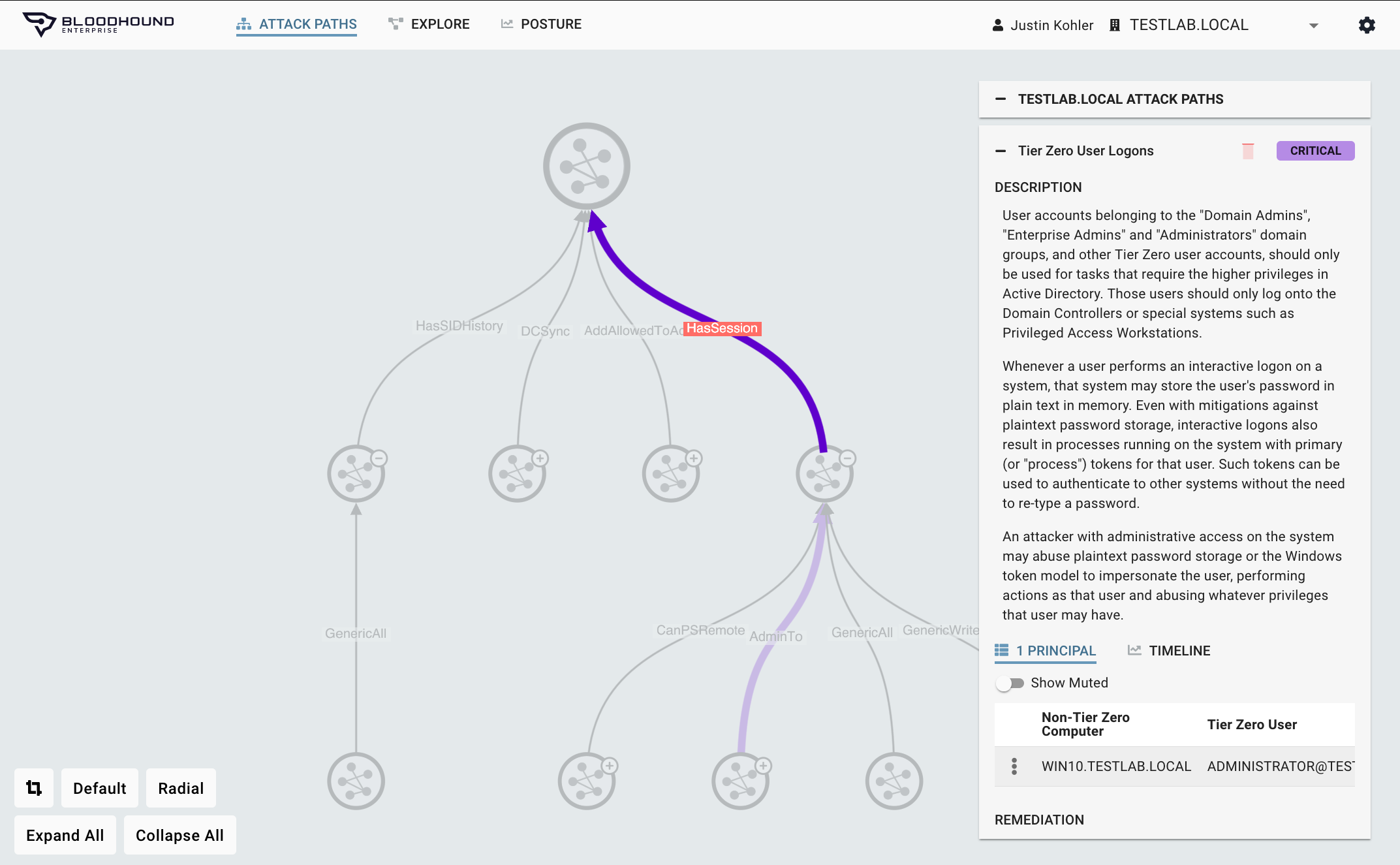
Comprehensive Visibility
Current Solutions Don’t Fit
BloodHound Enterprise exposes all the active pathways adversaries can take to move laterally and escalate privileges to Tier 0 principles. Even as your networks, user privileges, application permissions, and security group memberships change, BloodHound Enterprise continually:
- Maps every relationship and connection
- Provides full understanding of real permissions
- Tracks and exposes new Attack Paths
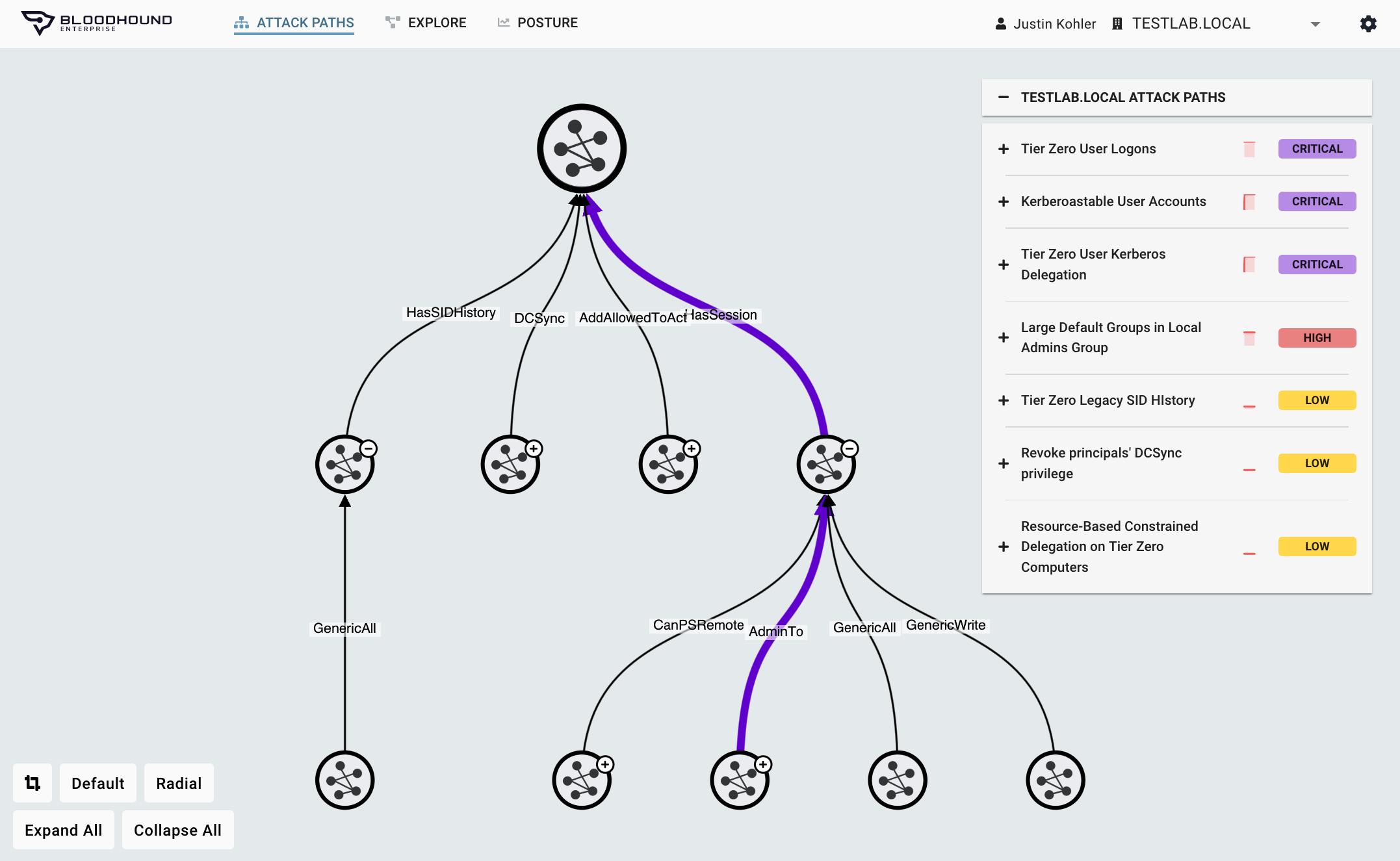
Prioritized Response
Risk-Based Choke Point Analysis
Exposing all the Attack Paths is just the first step. To stop adversaries in their tracks, BloodHound Enterprise identifies the optimal remediations by:
- Measuring the empirical exposure of each Attack Path
- Pinpointing Choke Points to block the largest number of pathways
- Ranking remediation Choke Points by collective risk reduction
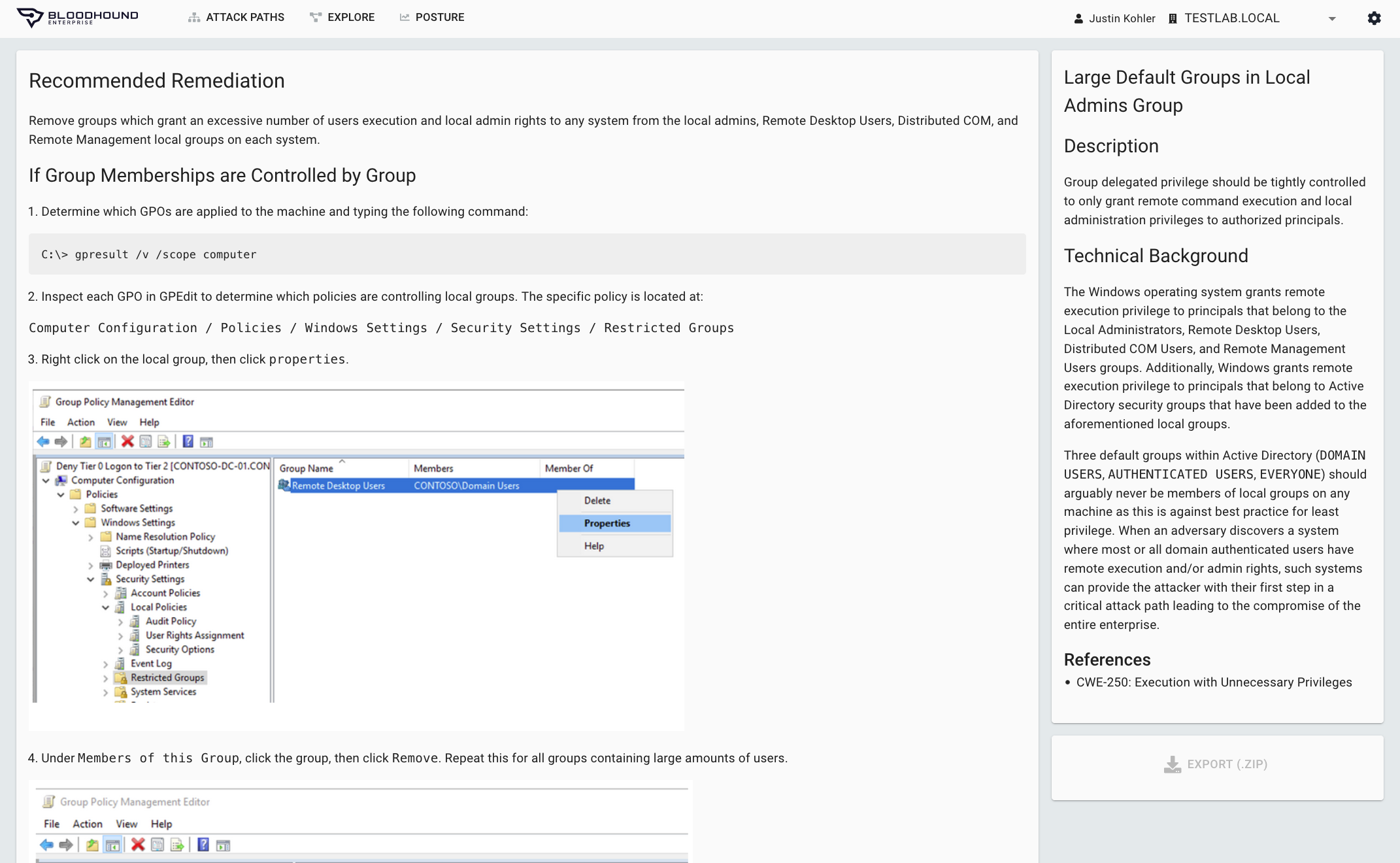
Remove Lateral Movement and Privilege Escalation
Real-World Remediation
Eliminating Attack Paths requires real-world guidance to ensure proper resolution. Based on understanding the true privileges of the users and the pathways they create, BloodHound Enterprise provides:
- Step-by-step guidance with pictures eliminates the guesswork of the specific configurations required to eliminate Attack Paths
- Pinpoint remediations require the least amount of change possible while removing the greatest amount of risk
- Expert guidance from our Technical Account Management team to prevent breaking changes