Privileged Access Governance and Compliance
Privilege access compliance – mandated by all, achieved by none
“Implement Least Privilege” sounds great but how can it actually be accomplished? Even the best AD and Entra ID designs in the pursuit of Zero Trust violate compliance with buried privileges and constant change.
-

Required Privileged Access Separation
Most compliance frameworks require that users maintain separate privileged accounts from their standard user accounts.
- NIST CSF v1.1 PR.AC-4: Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties
- NIST CSF 2.0 PR.AA-05: Access permissions, entitlements, and authorizations are defined in a policy, managed, enforced, and reviewed, and incorporate the principles of least privilege and separation of duties
-

The Unseen Problem
The complex relationships of users, systems, and privileges within AD and Entra ID make identifying these violations impossible with built-in tooling. This means awareness of unintended compliance violations in the form of the hundreds of thousands of Attack Paths in your organization remain unknown and unabated.
-

Compliance with a Purpose
Adversaries seek administrative control to accomplish their objective. Every framework seeks to enforce the same basic separation from privileged accounts for this reason.
Take back control with BloodHound Enterprise
BloodHound Enterprise provides immediate visibility to Tier 0 violations where privileged accounts are not separated from user accounts. Architects and practitioners can make changes within AD/Entra ID and in real time see if violations are created.
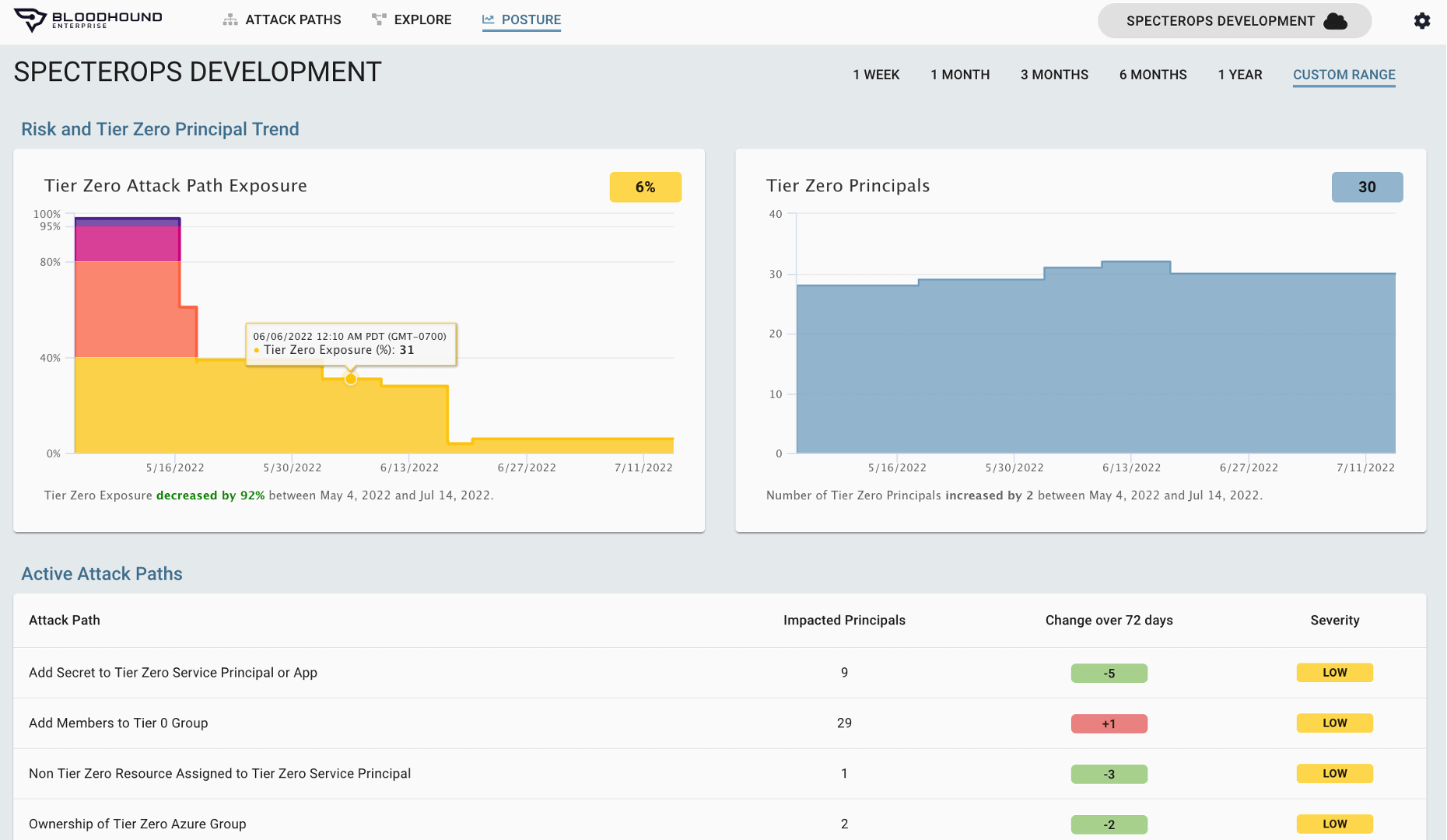
Violation Visibility
Identity Compliance Control
BloodHound Enterprise exposes all violations of privilege and user account separation. Even as your networks, user privileges, application permissions, and security group memberships change, BloodHound Enterprise continually:
- Maps every relationship and connection
- Provides you with a full understanding of real permissions
- Exposes new and existing compliance violations
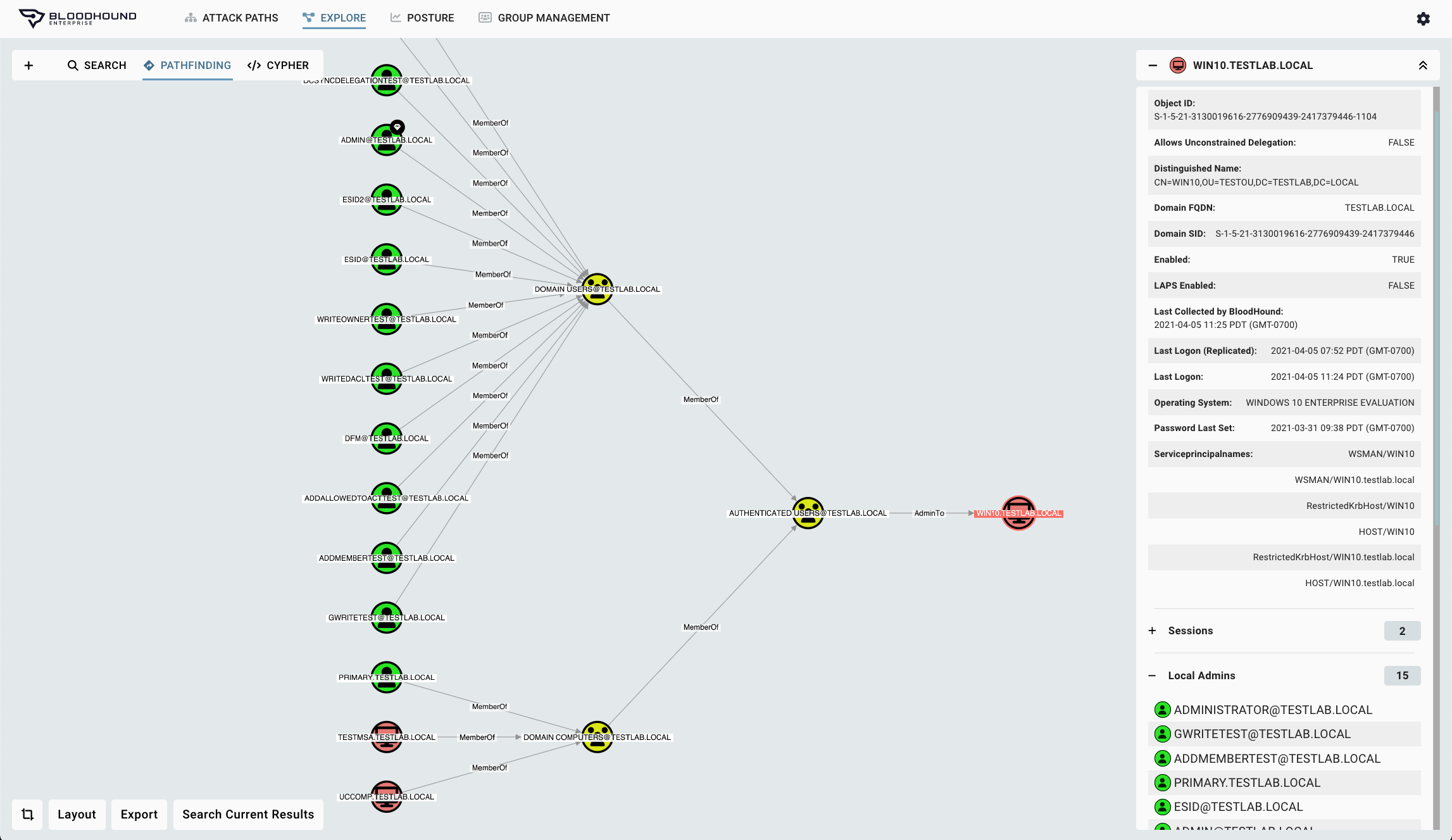
Violation Mitigation
Continuous Risk Assessments
Based on understanding the true privileges of privileged and user accounts, BloodHound Enterprise:
- Delivers practical remediations without drastic changes to AD / Entra ID or negative impact
- Provides precise and comprehensive remediation guidance to ensure compliance violation elimination
- Furnishes instructions on how to validate privileges being removed are not required
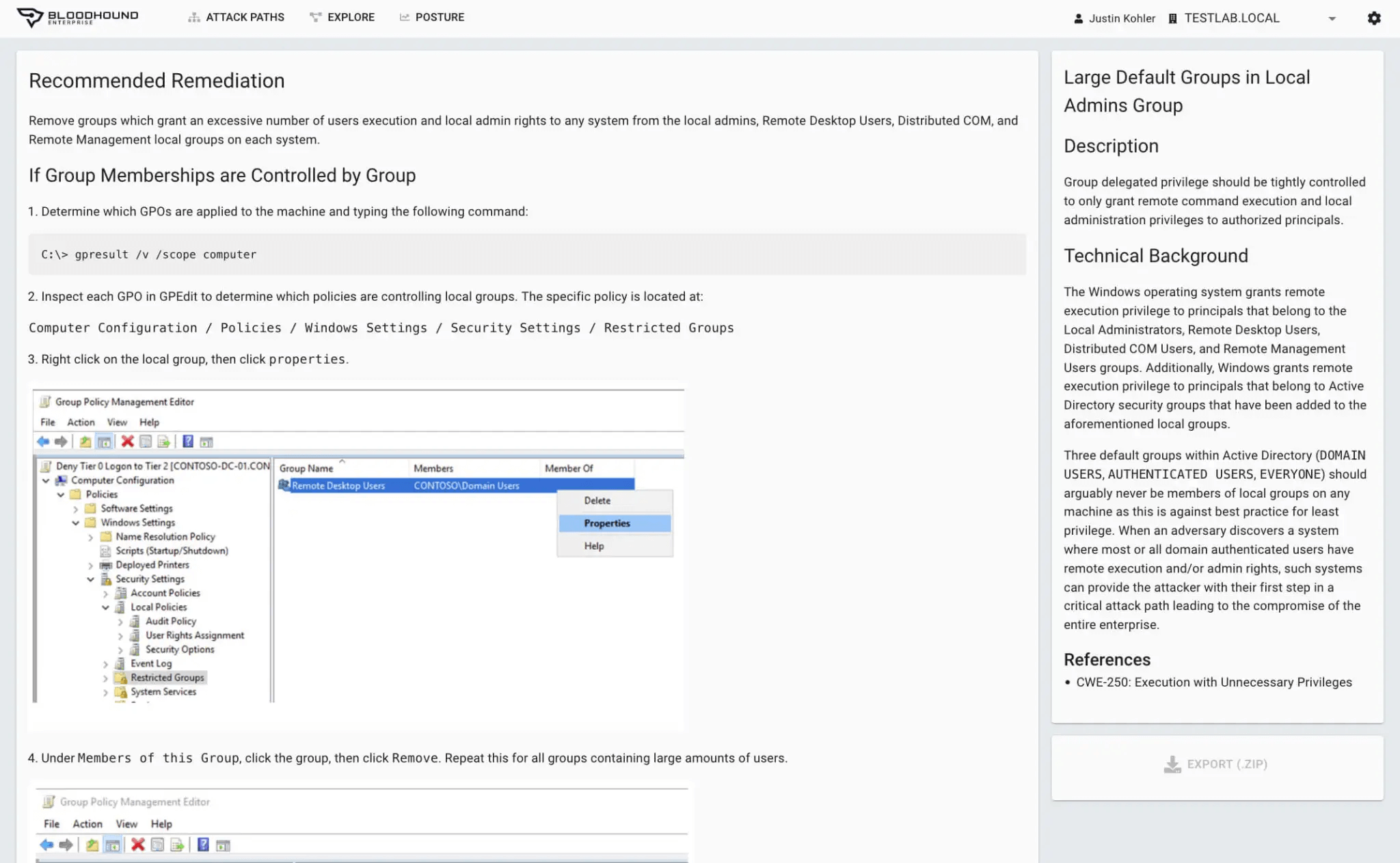
Compliance Reporting
Prove Your Compliance
Illustrate proper controls and processes are in place while being able to confidently report your compliance status.
- Report your Identity compliance with confidence
- Track your compliance over time
- Illustrate the effectiveness of your controls and processes