Active Directory Attack Paths — “Is everyone this bad?”
Active Directory Attack Paths — “Is it always this bad?”
We launched BloodHound Enterprise to help organizations manage Attack Paths in Active Directory (AD) a little more than three months ago. Since then, we’ve deployed into many environments and we run into some form of the same question every time, “so tell us, is it always this bad?” I wanted to quell some fears and ease some anxiety for those wondering the same thing when they run the open-source version by answering that question. So here it goes:
Yes, it’s this bad for everyone, you’re not alone.
By “this bad” folks are typically referring to the number or severity of the Attack Paths that we’re able to uncover immediately after deploying. Most teams go from zero to installed, collecting data, and viewing Attack Paths within thirty minutes and this first look can be quite jarring.
“Is it always this bad?”
While the answer is “yes”, it’s important to note why. Here’s a couple of the key reasons:
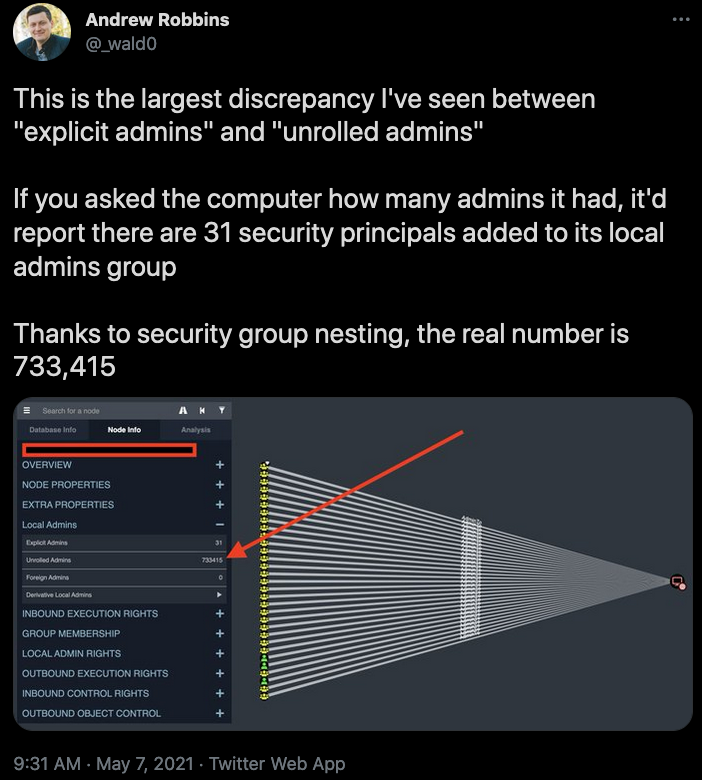
- Auditing privilege in AD is nearly impossible
- Lack of visibility has contributed to 20+ years of misconfiguration debt
Auditing privilege in Active Directory is nearly impossible
Auditing privilege in Active Directory has been nearly impossible prior to BloodHound Enterprise and is something we’ve discussed before. Ask any Active Directory administrator (we do often) how easy they think it is to understand where privileges are applied in the environment. Just answering the seemingly simple question of “which users have local administrator rights on this computer” can be painstakingly difficult. There’s no guarantee you’ll actually find the answer. In fact, something we started doing to really demonstrate how painful this is to our new hires is to walk them through how extraordinarily difficult this can be by using the built-in tools in Active Directory.
We like to hit on the opaque nature of privileges in Active Directory to really establish the fact that the resulting misconfigurations and Attack Paths are not the fault of some careless administrators. Active Directory admins are under extreme pressure maintaining the backbone of the enterprise and it’s a miracle they’re able to do so given the limited visibility they’ve had up to this point. They care about what they do and they care about the security of their systems. No admin would look at the effects of nesting groups below and think “yea this is fine.”
20+ years of misconfiguration debt
Now that we’ve established that lack of visibility is where this starts, let’s think about how long these problems have had to fester. Microsoft released Active Directory in 1999. There are people who work at SpecterOps that are younger than AD. While it’s been updated over the past 22 years (LAPS is great), it’s still more or less built on the same underlying functionality. While that speaks to the incredible resilience of these systems, there’s no doubting AD has its challenges (cough, visibility).
You can make a lot of configurations with a lot of unintended consequences over a 22-year period. Most admins are in their roles for 2–5 years before they either transition roles, move into management, or switch companies. That means that if your AD is reasonably young, let’s say 10 years old, you could have had 4–5 different administrative teams over that time period changing configurations. On top of misconfiguration debt, now we get to add tribal knowledge. This leads to equally familiar statements for us after we deploy; “I have no idea what that is” or “why that is there”. The reality is that BloodHound Enterprise is uncovering years, potentially decades, of misconfiguration debt in AD.
We’re doing things differently, better
This is why we created BloodHound Enterprise, to directly solve the problem of Attack Paths. The first look at a new organization can be quite jarring, but it’s the result of shining a light on a problem that’s been hiding in the dark for over twenty years. We’ve had the same question from smaller organizations with a single domain to Fortune 50 organizations with highly specialized and trained teams. It’s no one’s “fault” that this problem exists given the tools that have been available. Fortunately, there are a lot of quick wins available and granted the right visibility, we’ve demonstrated dramatic improvements in as little as twenty-four hours.
Yes, it’s this bad today, but today is where we start, and we now have the visibility and capability to fundamentally remove the adversary’s favorite target.
Active Directory Attack Paths — “Is everyone this bad?” was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.
